Recent attacks on European organizations
Deceptive Bytes’ research team detected in recent days a wave of attacks on European organizations, while the attacks are not that sophisticated, they employ social engineering to make users run a WSF script file from a zip file that would compromise the system and download a second stage payload using a PowerShell script running via a shortcut file, to mask the origin of the execution.
An example of a WSF payload
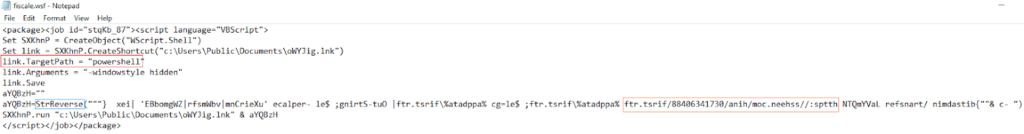
As seen, the shortcut’s target executable is PowerShell (in red) which is used to download the second payload, the URL (in orange) is written in reverse as the script uses VBScript’s StrReverse function (in blue) to reverse the payload, then it uses the saved shortcut to call the payload.
How Deceptive Bytes prevents such attacks
Deceptive Bytes’ platform blocks all unapproved scripts, reducing the attack surface on computers and servers in the enterprise.
Here’s a screenshot from one of our customers
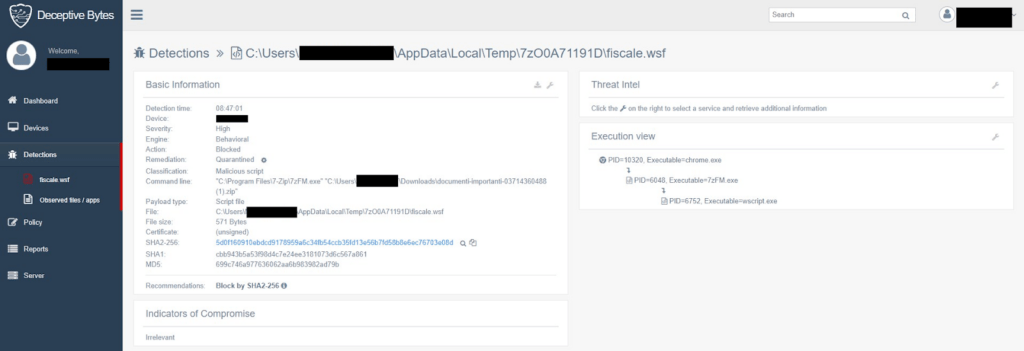
IOCs
SHA2-256 hashes (fiscale.wsf)
8e070c7e62ccf76a746618119f4ce7504c01a6d64197de92171773700c90fb7b
e9175a8c1f9ff3d6405ae04bb294101be5d5910d8ca14a98ba5dac563ea5979d
5d0f160910ebdcd9178959a6c34fb54ccb35fd13e56b7fd58b8e6ec76703e08d
Compromised URLs
https://ssheen[.]com/hina/03714360488/first.rtf
https://luanalt[.]com/luna/02546110350/doc.rtf
https://luanalt[.]com/luna/06620540481/lagos.txt
We suggest informing employees of these types of attacks & the way attackers engineer their emails to make users open such files. This would help reduce possible infection to unprotected environments.
Don’t Miss a Thing
Sign up today and we’ll send an email when new posts come out.
We collect and use this information in accordance with our privacy policy.


