Your proactive defense against Ransomware
Distort ransomware perception. Close the gap left by traditional security systems. Outsmart unknown and advanced attacks. Unmatched level of security. Never let your business down.
Think differently.
Protect proactively.
Stay ahead of the latest threats.

Preemptive defense
Create a hostile or unappealing environment for ransomware to operate, reducing its motivation and chances of infection.

Proactive defense
Continuously adapts the strategy based on the attacker’s behavior, effectively countering evolving threats.

Multi-layered approach
Seamlessly integrate with your existing security stack, enhancing your overall defense posture and providing an extra layer of protection.
Lightweight
No additional resources or operational overhead, ensuring business continuity without compromising security.
1
Agent
One user-mode process to prevent all types of threats
<0.01%
CPU
No scans means no unnecessary CPU usage
<20mb
memory
One user-mode process to prevent all types of threats
<1.5mb
Disk Space
Free of threats database means no unnecessary disk space is used
>99.9%
Prevention Rate
One user-mode process to prevent all types of threats
Here’s How we do it

Create
Create: generates deceptive information to stimulate and trick the ransomware

Disrupt
interferes with attackers’ attempts to spy on and infiltrate the environment

Prevent
manipulating the attacker’s perception prevents the execution of malicious intent
No further action is required!
Effective against
Key Features
Prevention First Approach
Focuses on disrupting attacks before they can execute
Easy to deploy and manage
Quick and easy deployment with minimal management overhead.
High stability
One user-mode process to prevent all types of threats
Signatureless
No constant updates and can operate in standalone / disconnected / VDI environments
High accuracy
Minimizes false positives and delivers high-fidelity alerts
Deployment flexibility
Deploy the management server on-premises, in the cloud, or in a hybrid setup to meet your environment's needs

Malware
Protection Engines
Ransomware Prevention
App Control
Behavioral
Anti-Malware
Firewall
Device Control
Core
Popular
Advanced
Pro
Capabilities
Deceptive Bytes Management Server
MSSP Multi-Tenant Management
Server Security & Access Control
Reporting
Executive C-Level Reporting
AI Assistant
Core
Popular
Advanced
Pro
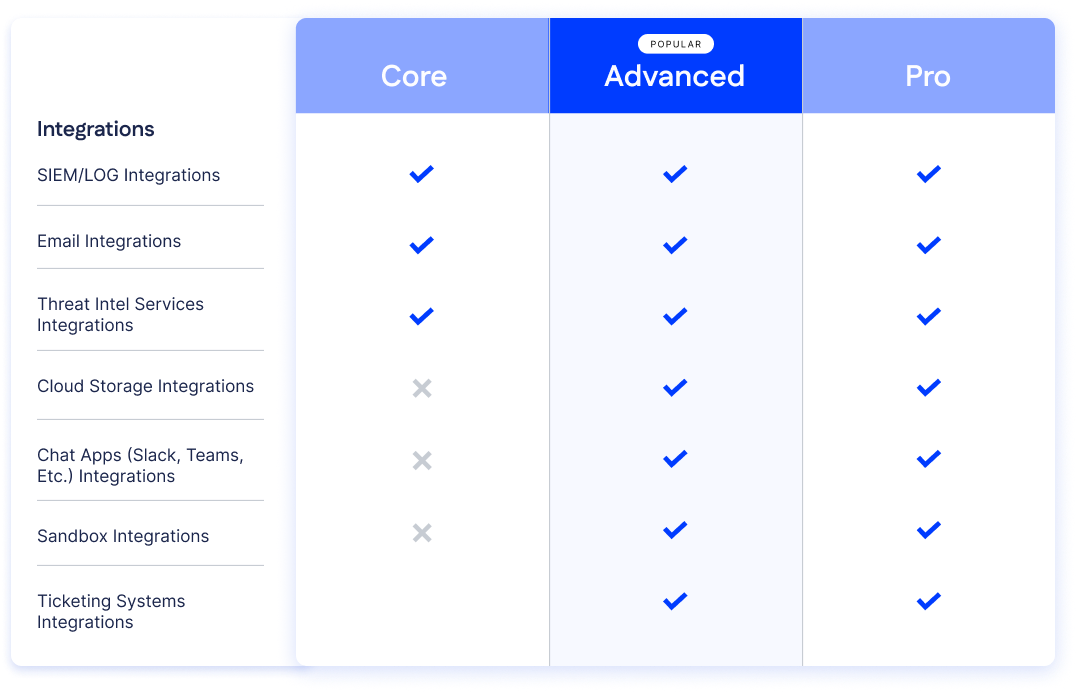
Integrations
SIEM/LOG Integrations
Email Integrations
Threat Intel services Integrations
Cloud storage Integrations
Chat Apps (Slack, Teams, etc.) Integrations
Sandbox Integrations
Ticketing systems Integrations
Core
Popular
Advanced
Pro
Compare Deceptive Bytes Packages


Compare Deceptive Bytes Packages
| Core | Advance | Pro | |
|---|---|---|---|
| Malware Protection Engines | |||
| Ransomware Prevention | |||
| Business Process Protection | |||
| App Control | |||
| Anti-Malware | |||
| Firewall | |||
| Device Control | |||
| Browser Protection | |||
| Office Apps Protection | |||
| Custom Protection |
| Core | Advance | Pro | |
|---|---|---|---|
| Capabilities | |||
| Deceptive Bytes Management Server | |||
| MSSP Multi-Tenant Management | |||
| Server Security & Access Control | |||
| Reporting | |||
| Executive C-Level Reporting | |||
| AI Assistant |
| Core | Advance | Pro | |
|---|---|---|---|
| Integrations | |||
| SIEM/LOG Integrations | |||
| Email Integrations | |||
| Threat Intel services Integrations | |||
| Cloud storage Integrations | |||
| Chat Apps Integrations (Slack, Teams, etc.) | |||
| Sandbox Integrations | |||
| Ticketing systems Integrations |




