Prevention by Deception
Active Endpoint Cyber Defense
In an ever growing advanced threat landscape, one solution is making a difference.
Providing a multi-stage protection that dynamically responds to threats as they evolve and beats the bad guys at their own game!
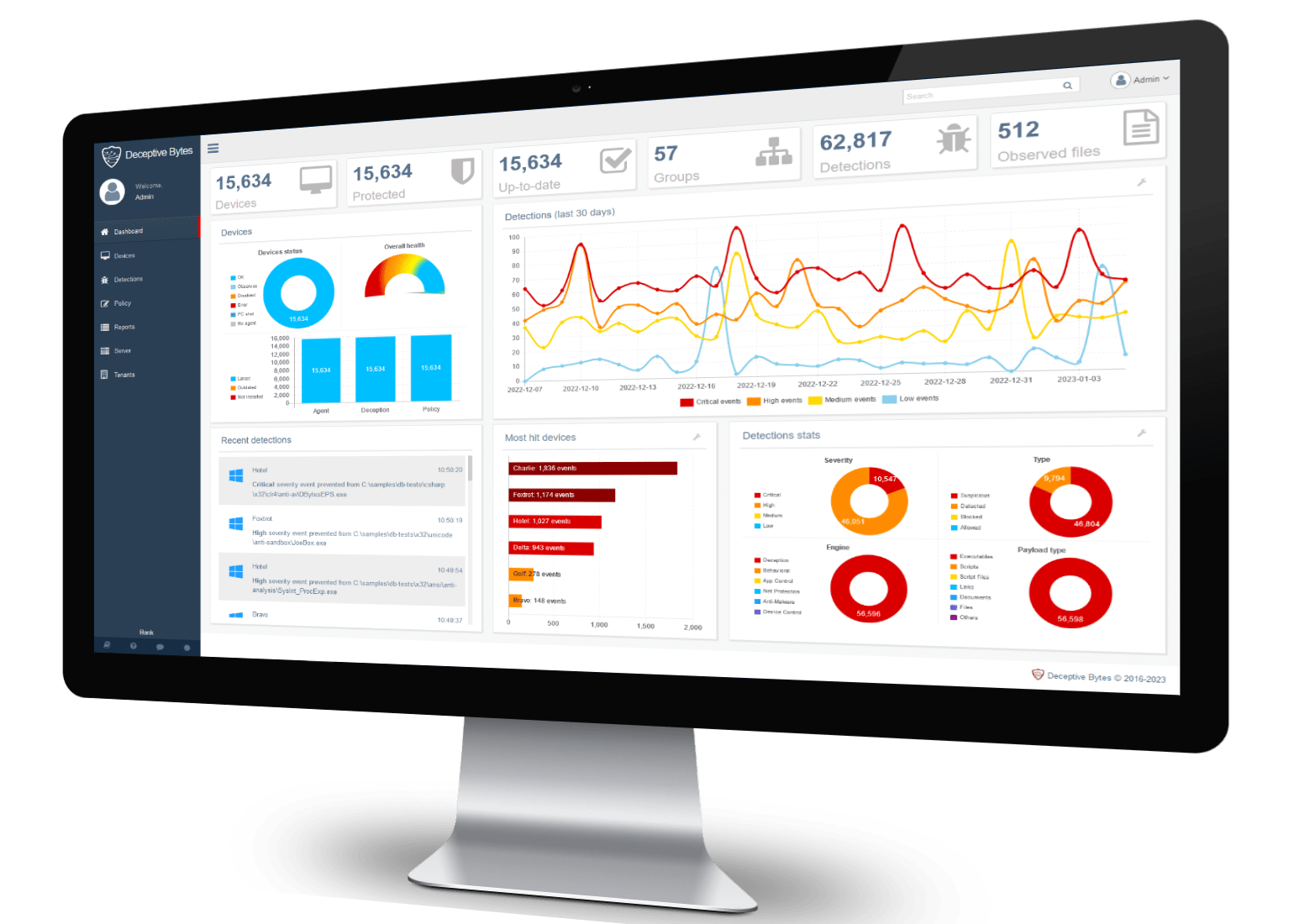
Over 99.9% prevention rate against ransomware & malware.
Our Mission
Help Improve security for
CISOS / IT MANAGERS
- Prevents Ransomware & Malware automatically
- Reduce alerts & false positives
- Adapt to changes in IT environments
- Operate in unpatched/vulnerable environments
ORGANIZATIONS
- Protect against unknown & sophisticated threats
- Reduce reputational risk
- Prevent damage to data & assets
- Reduce operational burden
C-LEVEL
- Reduce operational costs & resources
- Protect remote employees
- Improve employees' productivity
- Achieve higher ROI
MSSPs / INTEGRATORS
- Improve customers’ cyber resilience
- Control multiple customers using a single management server
- Change tactics from threat hunting to threat prevention
- Focus on customers’ other cyber threats/risks
"Every day, new tactics and techniques are emerging, ‘well established’ attacks remain successful and the threat from cyber espionage continues to grow. Deceptive Bytes’ Active Endpoint Deception provides a means to shape attackers’ decision making, manipulate their behaviors, and ultimately disrupt their effort to attack organizations
Sagi Lamay, CEO
The Solution
With Deception Inside
Deceptive Bytes provides an innovative solution against threats in enterprises’ most critical and exposed assets, their endpoints!
The solution creates dynamic & deceiving information which interferes with any attempt to recon the environment and deters any ransomware or malware from executing its malicious intents…
✓ Prevents unknown and sophisticated threats
✓ Very high prevention and detection rates
✓ Real time detection & response
✓ System-wide protection with pinpoint handling
✓ Deploys in seconds & Easy to operate
✓ Low resource usage (CPU, memory & disk)
✓ NO constant updates
✓ Operates in stand-alone/disconnected & VDI environments
✓ Stops millions of threats using only 1 evasion technique
✓ High stability – operates in User-mode
✓ Triggering high-fidelity alerts
✓ Low to non-existing false positive rate
Customer Testimonials
Among our customers







LATEST on OUR BLOG
learn what's new with us and in cyber security

Do you trust your EDR? Why it is not the endpoint savior (some) vendors claim it to be
Let’s start off by acknowledging that 10 years ago, the EDR brought a major paradigm change in the world of cyber security. It strengthened organizations

Deceptive Bytes appointed Gidon Pely as a board member
Deceptive Bytes is happy to announce Gidon Pely joining as its board member, helping in the strategic planning for the company’s growth. With over 25
Deceptive Bytes’ new solution for Linux is now available
Linux version of its Active Endpoint Deception solution with support for enterprise server distributions: Ubuntu, Debian, RHEL, and SLES.This new release will ensure that more

Detection Alert vs Prevention Notification
Since the dawn of cyber warfare, security professionals needed to react to an event as a dreadful alert pushed to their management console, alerting of





