Complete Solution
Overview
Uses malware's defenses against it
Shaping attackers decision making
At Deceptive Bytes, we understand the critical importance of safeguarding your digital assets against evolving cyber threats. That’s why we’ve developed groundbreaking technology that seamlessly operates alongside your third-party endpoint protection providers, enhancing your security measures and empowering your defense strategy.
Our innovative solution operates on multiple fronts, offering unparalleled versatility and effectiveness in combating malicious intrusions. Here’s how Deceptive Bytes can augment your security framework:
Preemptive Defense: Making malware believe it’s in an unattractive or hostile environment to attack, reducing its motivation and chances of infection.
Proactive Defense: Dynamically responding to threats as they evolve, and changing the outcome of the attack.

Prevent never-seen-before cyber-attacks
One user-mode process to prevent all types of threats
Operates when needed, no scans means no unnecessary CPU usage
Only necessary memory is used which lowers memory consumption
Free of threats database means no unnecessary disk space is used
Using malware defenses insures high prevention rate
Advantages
Simple, Effective!
Preemptive & Proactive
- Prevents unknown & sophisticated threats
- Very high prevention & detection rates
- Real time detection & response
Lightweight
- Extremely low resource consumption (CPU, RAM)
- System-wide protection with pinpoint handling
- Deploys in seconds
Signature-less
- NO constant updates
- Can operate outside the corporate network
- Stop millions of threats using 1 defense evasion
Reliable
- High stability - operates in User-mode
- Automatically approves legitimate processes
- Low to non-existing false positive rate
Why Choose Deceptive Bytes?
Innovative Technology
Our cutting-edge approach to cybersecurity harnesses the latest advancements in deceptive technology, staying ahead of evolving threats and adversaries.
Seamless Integration
With our solution's compatibility with third-party providers, you can enhance your security posture without overhauling your existing infrastructure.
Standalone Protection
For organizations seeking comprehensive security solutions or operating in environments with unique security requirements, Deceptive Bytes also functions as a standalone defense mechanism. By leveraging the power of deception, our technology proactively identifies and neutralizes threats before they can cause harm, offering peace of mind and safeguarding your assets against emerging risks.
Proven Effectiveness
Backed by rigorous testing and real-world deployments, Deceptive Bytes delivers exceptional results, protecting organizations of all sizes across diverse industries.
On-going Support
Our dedicated team is committed to supporting you at every step, providing assistance, updates, and insights to optimize your security strategy.
Effective Against
One agent to protect IT all
Among our customers







Solution Engines
Stop malware in Its tracks
Deception
Making malware believe it’s in an unattractive/hostile environment to attack & actively responding to it as it evolve - changing its outcome.
App Control
Manages applications' execution, allowing or blocking apps according to policy.
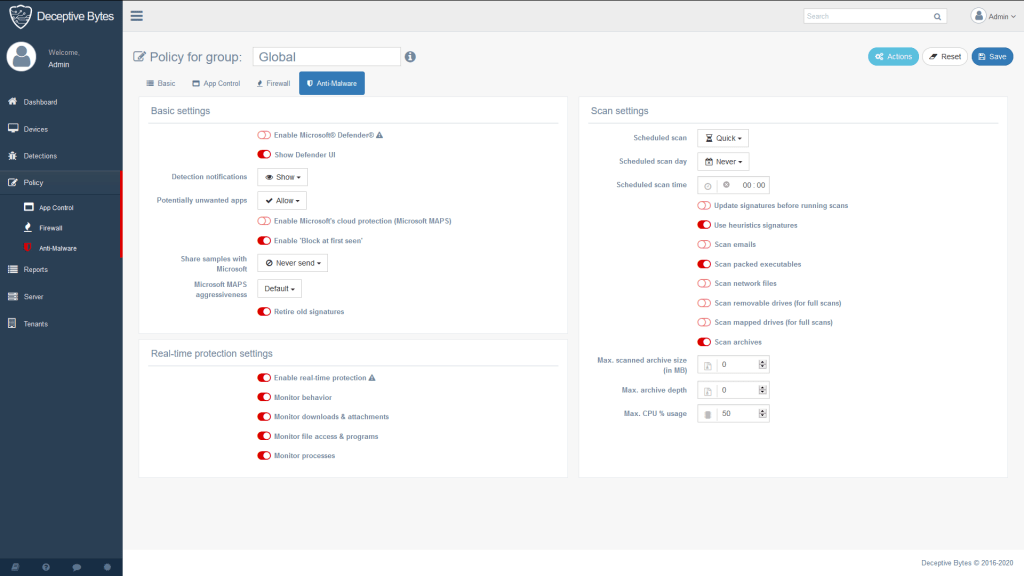
Anti-malware
Controls Windows Defender/Linux ClamAV settings on the endpoint through the management server and receive detections.
Behavioral
Protects legit applications used for malicious attacks.
Network Defense
Controls Windows Firewall/Linux UFW configuration on the endpoint.
Device Control
Manages security for connected devices on Windows machines
Solution Integrations
stronger Together
Windows Defender & Firewall
Linux ClamAV & UFW
When integrated to Windows Defender & Firewall/Linux ClamAV & UFW, the platform provides a comprehensive solution on the endpoint, giving defenders extra security layers to protect their endpoints without the added complexity, costs or burden.
Deceptive Bytes’ platform controls these solutions on one hand and get threat notifications on the other, giving full visibility when connected.